How to achieve Business Continuity by Preventing Data Loss?
This is a short movie of 4 minutes and 30 seconds depicting story about Mikesh, an IT manager who faces challenges and how he overcomes them. This is the story about an engineering company for which data is very critical and loss of this data can stop their business. Mikesh faces the biggest challenge while requesting employees to save data on central server so he can take backup of important data. As data is decentralized on employees’ desktops or laptops. It depicts how Mikesh forces employees to save data on central server, calmly deals with a laptop damage situation at the last moment as well as emerges unaffected after a ransomware attack.
What is the concept of Forced Centralization or Zero Data Scatteredness?
This is an animated movie on how a vigilant IT Manager brings some hard-headed users to the terms. Some users break the rules as they either do not understand the rules or they don’t want to follow the rules. Rule of Storing data on central server is such most neglected and broken rule in MSMEs. Users skip storing data on central server against the instructions by IT Manager and put entire enterprise at risk of Data Loss and Business Discontinuity. This 50 second video explains concept of Forced Centralization or Autocratic Centralization or Zero Data Scatteredness
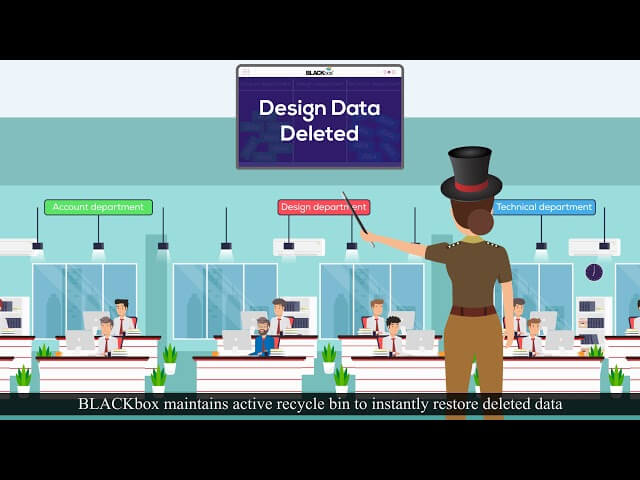
How to maintain business continuity when a user accidentally or intentionally deletes enterprise data with Active Recycle Bin technology? How to identify who deleted, when and what data.
This 2 minute 50 seconds short movie explains data deletion situation in the enterprises. Enterprises use shared folders with all important data among users to facilitate collaboration. A lot of investment goes into creating data. This movie explains about consequences if a user accidentally deletes all the data from shared folder. Not only that but also can the data be deleted intentionally also by some destructive user. This video explains how enterprise can restore deleted data to maintain its business continuity. Sometimes, data is deleted intentionally by users. It is critical for an enterprise to be able to identify who deleted the data. This video explains how BLACKbox’s active recycle bin technology lets enterprise maintain its business continuity in case of accidental or intentional deletion of data as well as identify who deleted data in case of intentional deletion.
How to maintain business continuity when a ransomware strikes? Plan B to rebound from Ransomware Attack when your antivirus fails
This 2 minute 30 seconds short movie explains particularly important strategy. Enterprises use Firewall and Antivirus to protect themselves from Virus or Ransomware attack. Having Firewall and Antivirus is a proactive strategy. That does not mean that you will never be affected by virus or ransomware. There is always a zero day. Firewalls and Antivirus take time to respond to new ransomware outbreaks. Such time window is known as zero day and enterprise is vulnerable even though they have antivirus. This video explains Vault and Workspace Technology which helps enterprises to recover data with minimum losses in minimum time after ransomware attack. This is always your plan B and you can be double sure. Even if your Firewall and Ransomware fail to detect ransomware, your business continuity is not affected as you can rebound in minimum time.
How to prevent Data Loss in event of Laptop Theft, Ransomware, Hardware Crash, Disaster
This 2 minute 20 seconds short movie explains how to maintain business continuity by preventing data loss in event of laptop theft, hardware crash, ransomware or disaster. It is innovatively pooled storage space on which data of all laptops, desktop, servers, BLACKbox is backed up in compressed and encrypted format. You can maintain business continuity in any such events.
How to prevent Competitive Vulnerability by Preventing Data Theft and Leakage?
This is a short movie of 6 minutes depicting story about Varun, a new joiner to a company generating confidential IPR, Designs, Drawings that have a great competitive value. Varun is contacted by a competitor to get all the data of a specific project for money. He tried various means to steal data. He tries to steal data on USB, by email attachment, by uploading on Internet but fails, check how. He then requests for permission to bring his own laptop at work (BYOD basis) and tries all means to steal the data. He fails miserably and all the evidences are recorded by BLACKbox system. He is fired and the enterprise prevents its competitive exploitation due to such a hostile and dishonest employee.
How to prevent Competitive Vulnerability by Preventing Data Theft and Leakage from Laptops?
This is a short movie of 2 minutes explains that confidential IPR, Designs, Drawings that have a great competitive value. When enterprises provide laptops to the employee or allow them to work from their own laptop (BYOD) the digital assets of the company can be leaked or stolen through USB, by email attachment, by uploading on Internet. It explains BLACKbox duo technology which compartmentalizes the laptop in personal and enterprise zone. Enterprise zone is subjected to all data leakage and theft prevention policies to protect enterprise’s confidential data.
How to prevent Competitive Vulnerability by Preventing Data Theft and Leakage from Mobile Phones and Tablets?
This is a short movie of 2 minutes 30 seconds explains that confidential IPR, Designs, Drawings that have a great competitive value. When enterprises provide mobiles/tablets to the employee or allow them to work from their own mobile/tablet (BYOD) the digital assets of the company can be leaked or stolen through USB, by email attachment, by uploading on Internet. It explains BLACKbox duo technology which compartmentalizes the mobile/tablet in personal and enterprise zone. Enterprise zone is subjected to all data leakage and theft prevention policies to protect enterprise’s confidential data.
How to maintain Business Continuity in Hardware Failure Situation?
This is a short movie of 1 minutes 30 seconds explains how hardware failure event leads to serious loss of business continuity. Hardware failure can also lead to data loss which could be irrecoverable. It explains Real Time Failover Technology of BLACKbox which supplied twin devices and are synced bit by bit. It ensures business continuity and prevents data loss in event of hardware failure.
How to enhance Performance while Large Files Handling?
This is a short movie of 1 minutes explains how large files of Autocad, 3D Studio, Corel, Photoshop, Scada, ETab etc can slow down file access over the network. It explains SSD caching and link aggregation technology of BLACKbox which uses caching technology boosted by multiple LAN throughput for enhancing user’s experience while accessing large files over network.
How to save 70% G-Suite Cost?
This is a short movie of 3 minutes explains how to save 70% on G-Suite subscription cost. MSMEs have majority of users who do not use all the features of G-Suite, but MSMEs have to pay full cost for such users. G-Suite with BLACKbox can save huge cost by dividing users (majority) who need plain vanilla email system and users (few) who need all the features and rationalize cost of G-Suite.
How can Forced Centralization force user to save data on central server only?
This is 2 minute short movie on how an irresponsible user break the rules by saving data on local device instead of server devics. As they either do not understand the rules or they don’t want to follow the rules. Rule of Storing data on central server is such most neglected and broken rule in MSMEs. Users skip storing data on central server against the instructions by IT Manager and put entire enterprise at risk of Data Loss and Business Discontinuity. This video explains concept of Forced Centralization or Autocratic Centralization or Zero Data Scatteredness
What is Active Recycle Bin Technology? How can it help Enterprise to recover accidentally or intentionally deleted data and identify who deleted data?
This 50 seconds short animated movie explains data deletion situation in the enterprises. Data is used by users over shared folders with all important data among users to facilitate collaboration. Generation of data is result of huge investment which makes it digital assets. Business continuity can be severely affected if some user accidentally deletes the data. Sometimes, data can be intentionally deleted by some destructive minded user. This video explains how enterprise can restore deleted data to maintain its business continuity. Sometimes, data is deleted intentionally by users. It is critical for an enterprise to be able to identify who deleted the data. This video explains how BLACKbox’s active recycle bin technology lets enterprise maintain its business continuity in case of accidental or intentional deletion of data as well as identify who deleted data in case of intentional deletion.
How to restore data after a ransomware attack? How to maintain business continuity after ransomware attack
This 1 minute short movie narrates the dire consequences of ransomware attack. Zero day is the time window when a novel ransomware or virus breaks out while firewalls and antiviruses of the world take time to push updates to all the deployment to detect them. This is the most vulnerable time window for any enterprise and surely gets affected by novel ransomware or virus during the zero day time window. It is very important to recover data with minimum losses in minimum time after ransomware attack. This is always your plan B and you can be double sure. Check this video to understand Data Versioning Technology.
How to take backup of BYOD or enterprise owned laptop? How to segregate users’ personal and enterprise data? How to make sure that only enterprise data is backed up?
This 3 minute short movie explains challenges of data backup from laptop which is on BYOD (Bring Your Own Device) basis or it is provided by the enterprise. It narrates how personal and enterprise data are mixed up on a laptop and how difficult it is to take backup of enterprise data only. It narrates data segregation technology and shows how only enterprise data is backed up without having to backup voluminous personal data which has large entertainment files and private data of employee to avoid exhaustion of storage and privacy breach of an employee. It narrates how data is backed up on data center in encrypted format over secured connection.
How to manage USB ports to prevent Competitive Exploitation by Preventing Data Theft and Leakage?
This is a short movie of 3 minutes depicting story about helpless owner of Digital Assets, owning confidential IPR, Designs, Drawings that have a great competitive value. He observes everyday in his office that employees are using USB ports freely. He is concerned about data leakage and theft for competitive exploitation. He is also worried about NDA (Non Disclosure Agreements) he has signed with his customers. The IT manager tried hard to manage USB ports but falls short of expectations. This video shows how an enterprise should manage USB ports to prevent Data Loss, Leakage and Theft.
How to manage Internet Controls to prevent Competitive Exploitation by Preventing Data Theft and Leakage?
This is a short movie of 3 minutes depicting story about enterprise generating of Digital Assets in the form of confidential IPR, Designs, Drawings that have a great competitive value. It is business requirement of the enterprise to provide Internet to all its employees especially working in sales and Research department. Enterprise owner is knowing about resourcefulness of Internet, at the same time he is worried about data leakage and theft over the Internet which can lead to competitive exploitation. This video demonstrates innovative and proprietary way to control the Internet by Data Isolation Technology which gives full Internet access to employees but protect data from theft and leakage.
Importance of Data Backup Versioning in Ransomware Situation? How to rebound from Ransomware Attack when your antivirus fails
This 1 minute short movie explains importance of versions of the backup. Most enterprises set up automatic backup of data at on daily basis. When there is infection or ransomware attack, most of the times, this backup drive is exposed and last good backup is overwritten by infected data resulting in data loss situation. This video explains how you can deal with such situation by a backup versioning technology.
Importance of Data Backup Versioning in Ransomware Situation? How to rebound from Ransomware Attack when your antivirus fails
This 2 minute 30 seconds short movie explains how duplicate data can slow down performance, exhaust storage spaces, create confusion on which file is latest and makes data management very difficult. This video explains the solution provided by BLACKbox by forcefully centralizing all data and removing duplicate files by an apt use of AI.
BLACKbox Founder interacting with honorable jury members on Doordarshan in Innovation India program
Explaining Ransomware Rebound Plan, Maintenance of Business Continuity after Ransomware Attack, Explaining Methods of Data Theft, Consequences of Data Theft on Competitiveness, Competitors’ Malintent, Hostile Employees, IPR Breach, Misuse of USB Ports, Misuse of Email Attachment, Misuse of Laptops, Misuse of BYOD, Misuse of Internet, Misuse of BCC (Blind Carbon Copy)
Data Loss Prevention, Laptop Backup, Vault Workspace, Disaster Response, Forced Centralization, Work from Home, Data Theft Prevention, Data Leakage Prevention, Laptop Security, BYOD Data Security, USB Usage Monitoring, Email Vigilance, BCC Intercept, Happy Hours, Data Theft Prevention on Internet, Work from Home with Data Security
BLACKbox Founder on film produced by FICCI
Explaining Ransomware Rebound Plan, Maintenance of Business Continuity after Ransomware Attack, Explaining Methods of Data Theft, Consequences of Data Theft on Competitiveness, Competitors’ Malintent, Hostile Employees, IPR Breach, Misuse of USB Ports, Misuse of Email Attachment, Misuse of Laptops, Misuse of BYOD, Misuse of Internet, Misuse of BCC (Blind Carbon Copy)
Synersoft was awarded Gold Medal and Cash Prize for its technology Innovation. This video is produced by FICCI, , Department of Science and Technologies – Government of India, Lockheed Martin Corporation – USA, IC2 Institute of University of Texas, Austin, Indo-US Science and Technology Forum under India Innovates Growth Program 2011.
Data Loss Prevention, Laptop Backup, Vault Workspace, Disaster Response, Forced Centralization, Work from Home, Data Theft Prevention, Data Leakage Prevention, Laptop Security, BYOD Data Security, USB Usage Monitoring, Email Vigilance, BCC Intercept, Happy Hours, Data Theft Prevention on Internet, Work from Home with Data Security
IT in a Box, All in One, BLACKbox
Explaining Ransomware Rebound Plan, Maintenance of Business Continuity after Ransomware Attack, Explaining Methods of Data Theft, Consequences of Data Theft on Competitiveness, Competitors’ Malintent, Hostile Employees, IPR Breach, Misuse of USB Ports, Misuse of Email Attachment, Misuse of Laptops, Misuse of BYOD, Misuse of Internet, Misuse of BCC (Blind Carbon Copy)
Data Loss Prevention, Laptop Backup, Vault Workspace, Disaster Response, Forced Centralization, Work from Home, Data Theft Prevention, Data Leakage Prevention, Laptop Security, BYOD Data Security, USB Usage Monitoring, Email Vigilance, BCC Intercept, Happy Hours, Data Theft Prevention on Internet, Work from Home with Data Security
Understanding on how to prevent misuse of emails from data leakage
This 2 minute 50 seconds short movie explains how email system can be misused to leak confidential enterprise data. It explains various methods of Data Leakage and Theft. Conventional DLP solutions may not work against such attempts of data leakage. It also explains how BLACKbox can serve as a layer between email host and email user to provide email vigilance and restrictions to prevent Data Leakage and serves as a practical DLP Solution.
Understanding the risks on enterprise data and available solutions
This 2 minute short video explains how the data is the most critical factor considering business continuity of the enterprise. It explains consequences of data loss by deletion, infection and disaster. It explains how enterprise can be competitively exploited by data leakage over USB, Internet and Email. It suggests the solutions to overcome these risks.
Podcast by Vishal Shah on – How to balance between Users’ Freedom and Prevent Data Leakage over Internet
This podcast describes innovative technology to trade the balance between Users’ freedom to access unrestricted Internet for research/business development and management’s concern to prevent data leakage/theft during the Internet session. We call it happy hours. It is a signature feature of BLACKbox. It has builtin data isolation technology which automatically unmounts enterprise data when the user switches to an unrestricted Internet session for research/business development.
Five Misunderstanding of MSMEs about IT and its logical clarification by Vishal Shah
This 11 minute podcast is specifically prepared for MSME Owners. Vishal Shah clarifies on five most common misunderstanding about IT in terms of Costs, Complexity, Security, Cloud, Ransomware, and Hardware. He takes a dig at each misunderstanding one by one and logically clarifies. It is about IT Policy Enforcement, Remote Application Access, Cloud Backup, Data Recovery after Ransomware Attack, and Purchase of Software/Hardware.
Short Movie: “Who Kaun Thi” (Who was that woman) with English Subtitles? How to maintain business continuity after data manipulation by the user or ransomware attack?
This is a short movie of 2 minutes explains a complex problem in entertaining and sporty way. Cricket is the most popular form of sports in India. People connect with cricket easily. This movie uses script based on the game of cricket to explan how hardware failure event leads to serious loss of business continuity. Hardware failure can also lead to data loss which could be irrecoverable. It explains Real Time Failover Technology of BLACKbox which supplied twin devices and are synced bit by bit. It ensures business continuity and prevents data loss in event of hardware failure.
Short Movie: “HumShakals” (Lookalikes) with English Subtitles? How to avoid complex and expensive IT Infrastructure by deploying IT in a Box product?
IT in a Box, All in One, BLACKbox
Explaining Ransomware Rebound Plan, Maintenance of Business Continuity after Ransomware Attack, Explaining Methods of Data Theft, Consequences of Data Theft on Competitiveness, Competitors’ Malintent, Hostile Employees, IPR Breach, Misuse of USB Ports, Misuse of Email Attachment, Misuse of Laptops, Misuse of BYOD, Misuse of Internet, Misuse of BCC (Blind Carbon Copy)
Data Loss Prevention, Laptop Backup, Vault Workspace, Disaster Response, Forced Centralization, Work from Home, Data Theft Prevention, Data Leakage Prevention, Laptop Security, BYOD Data Security, USB Usage Monitoring, Email Vigilance, BCC Intercept, Happy Hours, Data Theft Prevention on Internet, Work from Home with Data Security
Short Movie: “Judvaa” (Twin) with English Subtitles? How to maintain business continuity in the event of hardware failure by deploying IT in a Box product?
How to maintain Business Continuity in Hardware Failure Situation?
Explaining Hardware Failure Situation, Loss of Business Continuity
Short Movie: “Aankhe” (Eyes) with English subtitles? Concerned about the Data Leakage causing losses?
How to stop Data Leakage in your Organization?
Explaining Data Leakage, Indiser Threat, Loss and Theft